Virus Threats: Cryptolocker, Cryptowall and Cryptofortress
Background
Since 2013 there has been a widespread security threat for Windows computers through a new type of Trojan virus. It is disguised as an email attachment and, when opened, holds the user’s files for ransom. It encrypts data files such as Word documents and images on local and network drives and requests a monetary payment via credit card for files to be decrypted. The files are not useable until the ransom is paid.
We've had virus' before, why are these so bad?
These are ransomware, the new breed of viral threats. Historically virus writers were initially motivated by mischief; then viruses were used by spammers to both send spam and harvest email addresses. The latter had a financial benefit and accelerated the proliferation of new viruses and variants, though nowhere near as much as ransomware.
The new ransomware viruses are thought to be spread by cyber criminals, possibly Russian, who may even offer credit card processing for your ransom and a help desk in case you need support, unbelievable! According to Wikipedia (http://en.wikipedia.org/wiki/CryptoLocker) it's possible the criminals netted up to $23M in the first 3 months of CryptoLocker alone.
The latest wave (mid-end of March 2015) is specifically targeting Australia and those who have provided an email address in online advertising on Seek, Monster and newspaper job ads etc.
Emails to avoid
The virus is activated by clicking on links in emails apparently from such organisations as:
- Australia Post as false delivery notifications from "info@aust-post.biz" or similar, rather than their official austpost.com.au
- The email states that Australia Post was unable to deliver their parcel, and would be prompted to download the information
- NSW Office of State Revenue as Infringement notices
- The email states you have received either a parking or Traffic Infringement notice and must click to view it
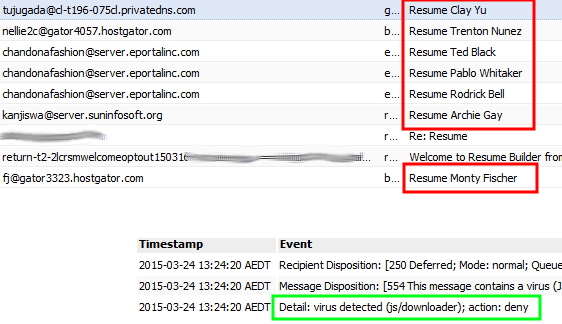
- Various individual names with a subject starting with "Resume " and containing various names

Activation
If you click on the attachment in the email, the virus will activate without any further signs. As you continue on, it is in the background silently encrypting your Organisations files.
 As yourself or others are viewing files stored on various systems, you may see these strange files, or your current files may have ".encrypted" at the end of the name. This is a sign you currently have, or have had an activated virus on your network.
As yourself or others are viewing files stored on various systems, you may see these strange files, or your current files may have ".encrypted" at the end of the name. This is a sign you currently have, or have had an activated virus on your network.
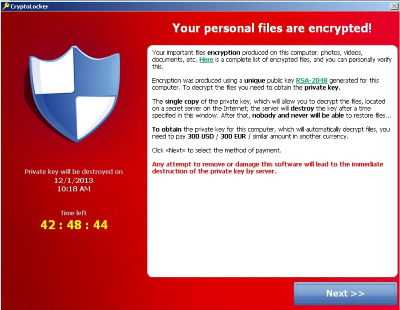 Once the virus is finished performing the encryption on your files, the PC that is running the virus will show this message to you - this is the ransom message.
Once the virus is finished performing the encryption on your files, the PC that is running the virus will show this message to you - this is the ransom message.
What if I see the above signs?
You need to act, FAST! It takes time for the files to be encrypted, so the faster the virus is identified and stopped, the less files will be affected.
- Call your IT support and advise you have seen virus behaviour
- Shutdown all workstations, particularly those running email, particularly if staff have clicked on any attachments
- Wait for further instructions from your IT support. The first step is to determine what is infected with the virus and to stop it encrypting files. Once that is done, it's a matter of restoring data from backups and putting in place any prevention measures that did not exist previously.
Why can't I just pay the ransom?
You can certainly opt to pay the ransom, it is believed around 3% of those targeted have chosen to do so. If you do not have backups and need your data, this may be your only available option.
There are a number of reasons why this may not be a good idea:
- It encourages further behaviour by the criminals
- It flags to them that you are vulnerable, you may be more specifically targeted in the future
- There have been versions of the Crypto virus which do not work correctly, so you might pay the ransom but end up without your unencrypted files
For some early versions of these Crypto viruses, thanks to law enforcement action, there are utilities available to decrypt your files using private keys recovered from criminals. This maybe an option if your encrypted data cannot be restored.
So how do I prevent it?
Given the large number of variations over recent years, the increase in Australia targets and the potential money earnt by criminals, we believe the frequency of these attacks will only increase. We believe it's inevitable that an infection will occur in your Organisation.
The philosophy to employ is "Defence in Depth" and not leave the job to one product or method.
We use various antivirus software vendors, as one may be better than the others to identify a new threat:
- Email scanning antispam/antivirus service. Our Service has caught and stopped a very large number of emails even getting to a persons mailbox
- Desktop and Server antivirus. We have recently employed a newer antivirus technology for our Desktop/Server Antivirus Service which works very well at detecting the latest viruses.
- Firewall with Universal Threat Management. The Cyberoam Firewalls we sell and implement have several measures which work well to provide a 3rd detection and mitigation layer
Much like the threats posed by fire and theft, having frequent copies of your data stored securely offline and off-site is the ultimate prevention. Once that is achieved, the closer your backup regime can lag the creation of the data, the better. There are backup methods available, for example, which take snapshots of data every 15 minutes, providing very recent and granular points in time where files can be recovered from. It doesn't have to be a copy from last week or last months backup.
Backup methods that can be employed:
- VSS based file backup schedule. Employed on the local system and Server it can provide the fastest recovery method. It is vulnerable to the Crytofortress virus however which will delete VSS copies on the infected system
- Off-system backup using VSS snapshots and copying of the data to a Network Attached Storage device. Can copy the data every 15 minutes, providing very granular file restoration
- Off-system file backup, including online/Internet based and tape copying. Requires good Internet connectivity (bandwidth), slow to restore if a mass file recovery is needed
- Off-site tape and disk pack rotation. We have a service which provides an secure transport and storage of your tape or disk material. The copy can be retrieved in a business day for cases where the onsite data is unavailable through fire or theft
Always be careful of what you download from the Internet and email attachments you open. Remember, you may be receiving the first copy of a virus which is not yet detected.
Cool Chilli has extensive experience in dealing with risks such as these. We can offer advice and services to help combat these threats.
